
A powerful anti-fraud system to protect your business
Prevent fraud at every stage of the user journey. C-SCORE analyzes data, detects suspicious activity, and alerts you to fraud in real time
Fraud costs businesses billions annually
5 - 15%
revenue
is lost from transactionfraud, bonus abuse, andmulti-accounting
10 - 20% is
reduced
due to low-quality trafficfrom unethical affiliate partners
Primary Fraud Types Detected
Fraud schemes are growing increasingly sophisticated. C-SCORE deploys advanced technology to detect and prevent fraud
Affiliate Fraud
Fake registrations, conversion inflation, arbitrage traffic
Payment Fraud
Stolen cards, chargebacks, money laundering schemes
Multi-Accounting
Using multiple accounts for system manipulation
Bonus Abuse
Multi-accounts, bonus farming, fraudulent promo code redemption

Alternative option for KYC and AML verifications
The voluminous data set and user-friendly interface will allow analysts of any team to make the fastest and best decisions regarding each individual player, stream, affiliate partner by more than 2.5 times
How C-SCORE Works?
Registration Data Analysis
Scrutinizes emails, phone numbers, IPs, and fraudster devices during sign-up
- Detects disposable emails and virtual numbers
- Uncovers hidden connections between accounts
- Filters out anonymous registrations
Registration Data Analysis
Scrutinizes emails, phone numbers, IPs, and fraudster devices during sign-up
Activity Monitoring
The system tracks user behavior, payment activity, and platform interactions
- User data reliability verification
- Continuous background user verification
- Suspicious pattern detection
Activity Monitoring
The system tracks user behavior, payment activity, and platform interactions
Predictive Analytics
The system learns from real data to forecast fraud scenarios
- Automatic detection of emerging fraud schemes
- Background suspicious activity scoring
- Customizable trigger-response framework
Predictive Analytics
The system learns from real data to forecast fraud scenarios
Automatic Notification
When a foul is detected, the system notifies you of the anomaly, allowing you to decide whether to reject the transaction or request additional verification
- Actionable data to block suspicious users
- Customizable trust/risk thresholds
- Seamless KYC & AML system integration
Automatic Notification
When a foul is detected, the system notifies you of the anomaly, allowing you to decide whether to reject the transaction or request additional verification
C-Score uses advanced technologies
Registration Data Analysis
Scrutinizes emails, phone numbers, IPs, and fraudster devices during sign-up
Detects disposable emails and virtual numbers
Uncovers hidden connections between accounts
Filters out anonymous registrations
Activity Monitoring
The system tracks user behavior, payment activity, and platform interactions
User data reliability verification
Continuous background user verification
Suspicious pattern detection
Predictive Analytics
The system learns from real data to forecast fraud scenarios
Automatic detection of emerging fraud schemes
Background suspicious activity scoring
Customizable trigger-response framework
Automatic Notification
When a foul is detected, the system notifies you of the anomaly, allowing you to decide whether to reject the transaction or request additional verification
Actionable data to block suspicious users
Customizable trust/risk thresholds
Seamless KYC & AML system integration
C-SCORE detects a fraud in the background
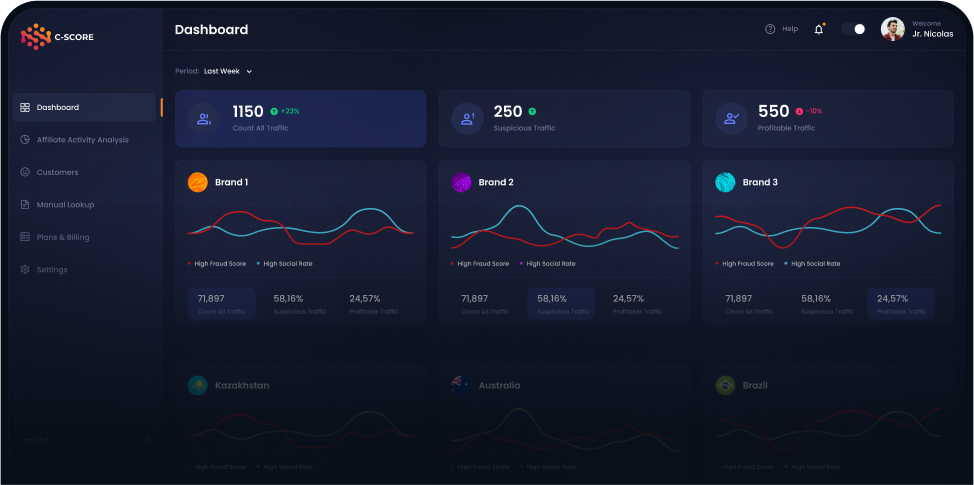
How much you can save with C-SCORE
Try C-SCORE and protect your platform from multi-accounts
Fill out the feedback form and find out how your business can go beyond standard protection and achieve tangible growth